On the Internet, not everything is what it seems to be. Hackers and scammers worldwide not only can pretend to be someone else but also copy legit software to inject it with malicious features. That’s the case (again) with several trading apps for cryptocurrencies. They might be infected with the crypto-stealing malware dubbed ‘AppleJeus’.
The cybersecurity firm Volexity has been studying a new campaign of that malware since June 2022. Those responsible for this virus would be the North Korean hackers known as Lazarus Group. Their goal is likely monetary benefits from unwilling victims worldwide. But they also gather all the information they can from devices —perhaps to prepare for further attacks.
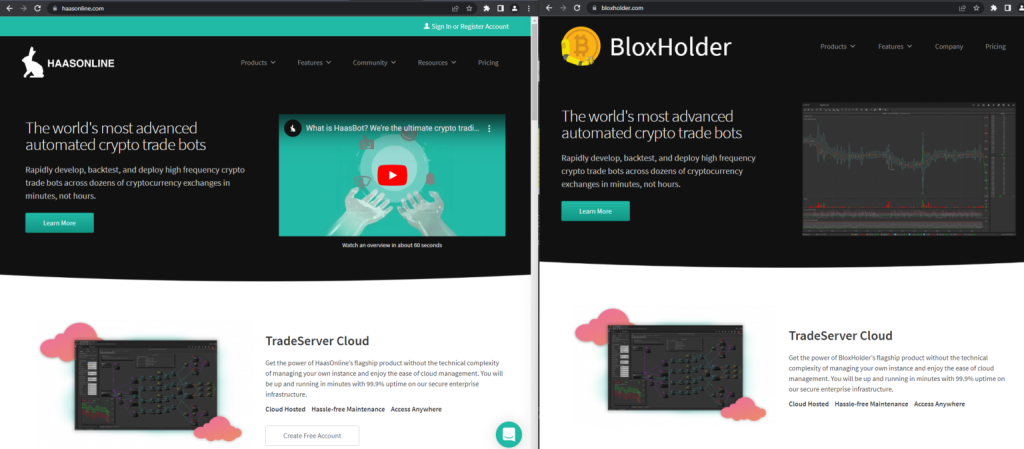
For this campaign, they registered the website domain “BloxHolder” and pretended to offer automatic trading with cryptocurrencies. However, the entire site and its app are only clones of the legitimate services offered by HaasOnline. Once the trader falls into the trap and installs the app, the crypto-stealing malware is also installed on the device and starts looking for wallets to empty.
Since October 2022, it was discovered that the hackers also distributed infected Microsoft Office documents —probably through mail and Telegram. These come with the AppleJeus ready to escape into the host system and look for 암호 화폐 to steal. One of the malicious documents was named “OKX Binance & Huobi VIP fee comparision (sic)”, which implies that they’re especially targeted at crypto users.
“BloxHolder” isn’t the only malicious brand, either. This malware has been registered since 2018 and has used a whole list of fake services and names to attract new victims. Among the names they’ve adopted are Ants2Whale, Celas Trade Pro, JMT Trading, Union Crypto, Kupay Wallet, CoinGoTrade, and Dorusio.
How to avoid crypto-stealing malware
As we may guess, it’s quite important to check for previous reviews before using any platform. Especially, any platform that involves money, and any crypto-related platform. Other security measures for users are basic: download software only from official and reputed sites, keep on and update their antivirus, prepare backups, and pay attention to potentially fake services.

Protection could be more complicated for organizations since they need to teach their employees about cybersecurity. Nevertheless, the Singapore Computer Emergency Response Team (SingCERT) has offered some institutional advice about this crypto-stealing malware beyond the basics:
- “Install a Host Based Intrusion Detection (HIDS) software and keep it updated to detect the latest indicators of compromise (IOCs) attributable to AppleJeus malware versions
- Specifically, cryptocurrency platform providers should also verify their compliance with the Cryptocurrency Security Standard at https://cryptoconsortium.github.io/CCSS (…)
- Isolate impacted host(s) from their network(s)
- Change all passwords to any accounts associated with impacted host(s) and enable two-factor authentication (2FA), if available
- Restore impacted host(s) from previous uninfected backups
- Generate new keys for cryptocurrency wallets and/or move to new wallets
- Use hardware cryptocurrency wallets which keep the private keys in a separate and secured storage area.”
The last tip could also apply to individual users, indeed. It’s important to keep your 개인 키 safe and, if possible, out of the Internet all the time.
BTC, ETH, 그리고 다른 토큰을 거래하고 싶으신가요? 가능합니다. 안전하게 Alfacash에서! 그리고 우리가 이 주제와 다른 많은 주제에 대해 소셜 미디어에서 이야기하고 있다는 것을 잊지 마세요.








