Even in a bearish market, hackers and scammers worldwide are looking for unaware victims. They’re using old and new technics to empty crypto wallets right now, or more than this, to steal energy and mine new coins. Therefore, it’s very important to know, at least, the most popular crypto-stealing malware.
There are simple ways to take care of your private keys and funds. The bad signals are also tale-telling at some point. However, it’s also easy to ignore them —or not know them in the first place. So, let’s go to explore some common infections in 2022, and how to avoid them.
Glupteba and other cryptojackers
This kind of crypto malware isn’t exactly for stealing cryptocurrencies. Instead, once installed on the computer or running from a malicious Internet window, it starts to steal energy and hardware resources. The purpose is to mine new coins (usually Monero) and send them directly to the hacker(s). This way, the operators don’t spend a cent on energy or computers but keep the tokens anyway.
Besides, probably the major problem with cryptojackers is that they’re very stealthy. The malicious software tries to take as less resources as possible (to go unnoticed) from as many machines as they can. So, cryptojackers are commonly mixed with “botnets”: networks of bots designed to control a massive number of devices at the same time.

The dubbed “Glupteba” is one of those cryptojackers-botnets. As described by Analiza łańcuchowa, it successfully infected over one million machines only in 2021. After silently kidnapping these devices, the hackers used them to mine Monero. Meanwhile, the victims barely experienced some lagged machines —their hardware, software, and energy being dried out.
Cloud and data companies, GPU farms, and maybe even some górnicy kryptowaluty are the favorite targets for cryptojackers since they have more power to offer. But this doesn’t mean that any computer can’t be kidnapped too. For the hackers, the more infected devices, the better.
RedLine and info stealers
The so-called info stealers can take much more than just cryptocurrency. They’re designed to find (and steal) saved credentials, files, history, cookies, banking data, and crypto-wallets inside the infected device. And they can do many more, if not controlled.

RedLine is a well-known info stealer, available for anyone. Not for anyone to be infected with (also that, though), but for anyone to buy from the Darknet. It’s even cheap: $150 for monthly access and $800 for lifetime access. And it includes a whole deal with additional (and malicious) tools. Like Chainalysis discovered:
“Buyers also get access to Spectrum Crypt Service, a Telegram-based tool that allows cybercriminals to encrypt Redline so that it’s more difficult for victims’ antivirus software to detect it once it’s been downloaded. The proliferation of cheap access to malware families like Redline means that even relatively low-skilled cybercriminals can use them to steal cryptocurrency.”
Moreover, według the Center for Internet Security (CIS), RedLine can also have remote functionalities and allow the installation of more types of malicious software.
(Fake) DeFi wallets
Decentralized Finance (DeFi) platforms are quite popular these days, and hackers know this. The ones that aren’t very busy stealing directly from DeFi protocols are dedicated to spreading fake DeFi wallets. Through social media or email, they promote these fraudulent apps and wait for victims.
Once inside a device, the crypto malware actually installs a functional DeFi wallet, along with a Trojanized one. The malicious app replaces the legit one, and the Trojan starts to work silently. It’s a backdoor designed to steal information and even control the device at a certain level. Kaspersky Lab identified the criminal North Korean group Lazarus as responsible for this campaign.
Previously, the firm also identified the group BlueNoroff as responsible for several attacks on cryptocurrency companies and users. Like the malicious app by Lazarus, the backdoor spread by this group checks the transaction history of the victim —if they’re crypto users. Then, even if the victim used a hardware wallet, the hackers just waited for a new transaction to happen in connection with MetaMask (widely used for Web3).
At that moment, the malware would change the original parameters of MetaMask in Google Chrome. They’d change the original destination address and amount to empty the wallet.
“When the compromised user transfers funds to another account, the transaction is signed on the hardware wallet. However, given that the action was initiated by the user at the very right moment, the user doesn’t suspect anything fishy is going on and confirms the transaction on the secure device without paying attention to the transaction details (…) the attackers modify not only the recipient address, but also push the amount of currency to the limit, essentially draining the account in one move.”
CryptoWall and more
The ransomware already pushed the United States and Costa Rica into a national emergency. This is a kind of malware that, once installed on the device or network, encrypts all personal files (documents, images, audio, video…) or the entire hard drive and asks for a ransom, often in cryptocurrency, to return them.
This crypto malware is especially dangerous for companies with commercial secrets, and for organizations like governmental agencies (full of private data from citizens) and hospitals (whose vital machines stop working). That’s why the hackers use to ask for millionaire ransoms as soon as possible.
The variant dubbed “CryptoWall” has been around since 2015, but it’s shown changes over the years. The last version, 4.0, improved its communication capabilities, also encrypted the name of the files, and included localized messages for the victims —they were delivered in English, French, or German according to the country.
CryptoWall arrives in their infected devices via email. Most ransomware is affecting companies and other big players lately, but they never stopped the infection of personal computers worldwide, either.
HackBoss and peers
Sadly, clippers aren’t a widely known crypto malware. They hijack the clipboard in the user’s device and detect when a crypto wallet address is copied by the owner. Then, this one is replaced for the hacker wallet address. So, if the user doesn’t pay attention, they may end up sending the funds to the wrong destination.
As explained by Chainalysis, “HackBoss” has been the more prolific clipper since 2012. The culprits have succeeded in stealing over $560,000 in Bitcoin (BTC), Ethereum (ETH), XRP, and other assets.
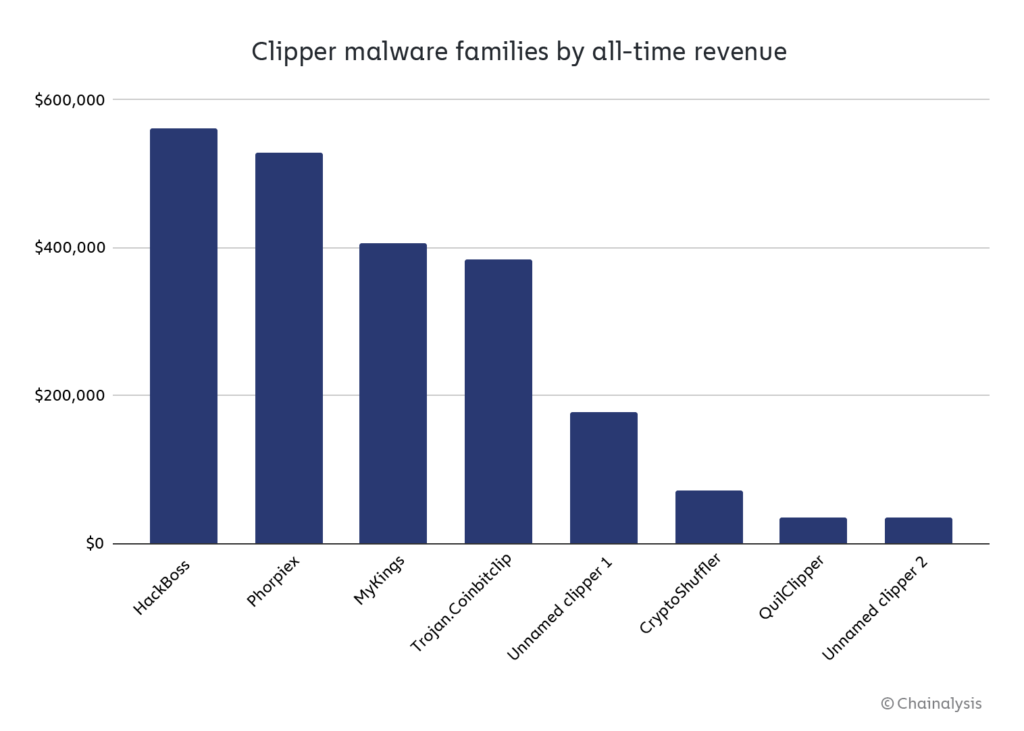
Clippers may not be like the billionaire ransomware industry, but they’re probably more dangerous to common people. They don’t offer any red flag to identify the infection upon arrival, and it’s very common to copy and paste the long crypto addresses for transactions. That mix could lead to high losses if the victim doesn’t pay any attention.
Unikaj złośliwego oprogramowania, które kradnie kryptowaluty
Over $14 billion in cryptocurrencies were stolen in 2021, według Chainalysis. That’s almost an 80% increase in illicit activity, compared to 2020. No wonder, considering that the crypto adoption also increased exponentially. Nevertheless, “transactions involving illicit addresses represented just 0.15% of cryptocurrency transaction volume in 2021”, as they explained.

We can conclude that most crypto activity is legit, but with more adoption comes more crimes as well. Then, it’s important to remember some basic security measures.
- Keep updated on the OS, antivirus, and firmware of all your smart devices.
- Nie otwieraj linków ani załączonych plików z podejrzanych e-maili.
- Download files and software only from the official websites.
- Make backups of all your important information and files on external devices, preferably offline.
- Avoid phishing sites and apps by looking at previous reviews and the URL, which is always different from the original.
- Pay attention to the news of your favorite websites and services: they should announce their customers if they’re under cyberattack.
- Double-check the wallet addresses! Compare and verify your original address and the pasted version twice before sharing or sending.
Wanna trade BTC, ETH, and other tokens? You can do it bezpiecznie na Alfacash! I nie zapominaj, że rozmawiamy o tym i wielu innych rzeczach w naszych mediach społecznościowych.
Telegram * Instagram * Youtube *Facebook *Świergot








